The AWS Cloud Migration Process
here may be some cases where you contemplate large legacy migrations in isolation, however, we are finding that migrations are usually part of a larger enterprise transformation effort. The patterns we have seen around migrating to the cloud commonly follow a 5-phase approach:

Phase 1: Migration Preparation and Business Planning
Here you determine the right objectives and begin to get an idea of the types of benefits you will see. It starts with some foundational experience and developing a preliminary business case for a migration. This requires taking your objectives into account, along with the age and architecture of your existing applications, and their constraints. We have partners such as RISC Networks, Atadata, Cloudamize, TSOLogic, and Apptio that have experience in this area.
Next, you need to understand your IT portfolio, the dependencies between applications, and begin to consider what types of migration strategies you will need to employ to meet your business case objectives. With the portfolio discovery and migration approach, you are in a good position to build a full business case. If you need help with understanding your IT portfolio, you can work with partners such as RISC Networks, Cloudamize, and Atadata as well as use AWS Application Discovery Service.
Phase 3 & Phase 4: Designing, Migrating, and Validating Application
Here the focus moves from the portfolio level to the individual application level and you design, migrate, and validate each application. Each application is designed, migrated, and validated according to one of the six common application strategies (“The 6 R’s”). Once you have some foundational experience from migrating a few apps and a plan in place that the organization can get behind - it’s time to accelerate the migration and achieve scale. Partners such as Cloudendure, CloudVelox, Atadata, Racemi, and Attuinity can help you here as well as AWS Server Migration Service (SMS) and AWS Database Migration Service (DMS).
Phase 5: Operate
As applications are migrated, you iterate on your new foundation, turn off old systems, and constantly iterate toward a modern operating model. Your operating model becomes an evergreen set of people, process, and technology that constantly improves as you migrate more applications. We have partners such as AppDynamics, NewRelic, and Dynatrace that can help you continue to iterate on your operating model as you move more to the cloud.
Organizations usually begin to think about how they will migrate an application during Phase 2 of the migration process. This is when you determine what is in your environment and the migration strategy for each application. The six approaches detailed below are common migration strategies employed and build upon “The 5 R’s” that Gartner outlined in 2011.
You should gain a thorough understanding of which migration strategy will be best suited for certain portions of your portfolio. It is also important to consider that while one of the six strategies may be best for migrating certain applications in a given portfolio, another strategy might work better for moving different applications in the same portfolio.
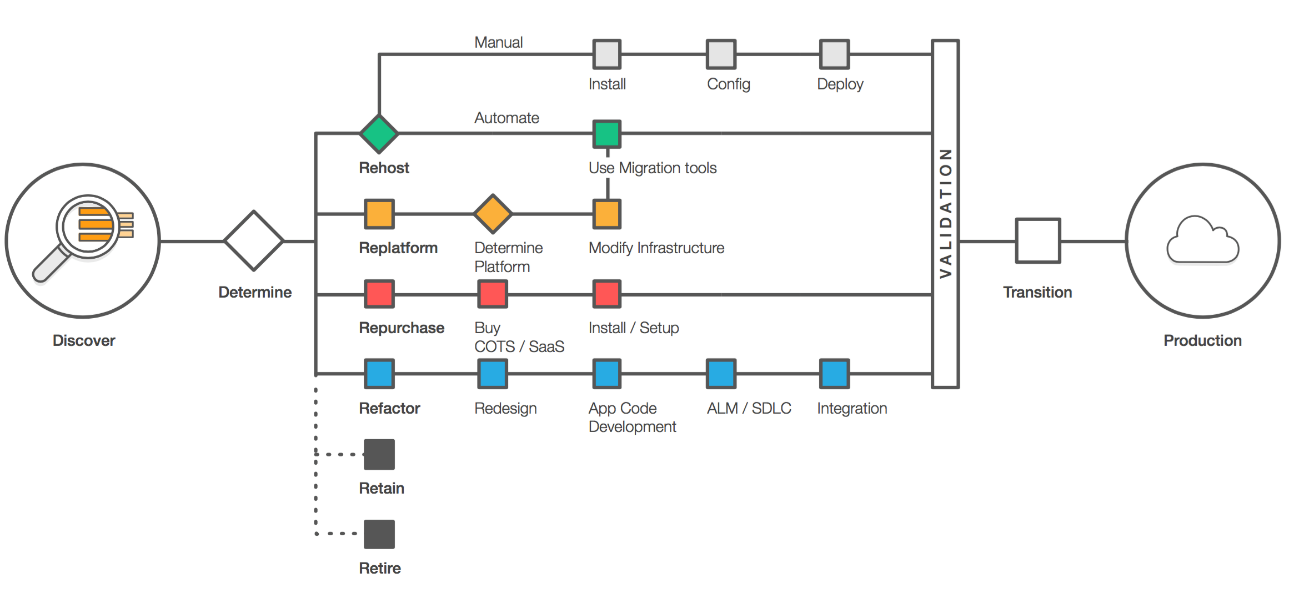
1. Rehost (“lift and shift”)
In a large legacy migration scenario where the organization is looking to quickly implement its migration and scale to meet a business case, we find that the majority of applications are rehosted. Most rehosting can be automated with tools such as AWS SMS although you may prefer to do this manually as you learn how to apply your legacy systems to the cloud.
You may also find that applications are easier to re-architect once they are already running in the cloud. This happens partly because your organization will have developed better skills to do so and partly because the hard part - migrating the application, data, and traffic - has already been accomplished.
2. Replatform (“lift, tinker and shift”)
This entails making a few cloud optimizations in order to achieve some tangible benefit without changing the core architecture of the application. For example, you may be looking to reduce the amount of time you spend managing database instances by migrating to a managed relational database service such as Amazon Relational Database Service (RDS), or migrating your application to a fully managed platform like AWS Elastic Beanstalk.
3. Repurchase (“drop and shop”)
This is a decision to move to a different product and likely means your organization is willing to change the existing licensing model you have been using. For workloads that can easily be upgraded to newer versions, this strategy might allow a feature set upgrade and smoother implementation.
4. Refactor / Re-architect
Typically, this is driven by a strong business need to add features, scale, or performance that would otherwise be difficult to achieve in the application’s existing environment. If your organization is looking to boost agility or improve business continuity by moving to a service-oriented architecture (SOA) this strategy may be worth pursuing - even though it is often the most expensive solution.
5. Retire
Identifying IT assets that are no longer useful and can be turned off will help boost your business case and direct your attention towards maintaining the resources that are widely used.
6. Retain
You may want to retain portions of your IT portfolio because there are some applications that you are not ready to migrate and feel more comfortable keeping them on-premises, or you are not ready to prioritize an application that was recently upgraded and then make changes to it again.
This is such great information. I have been looking for migrating to the cloud. While reading your post most of my questions were answered. Thanks so much for your helpful post.
ReplyDeleteA big decision when moving to the cloud is whether to choose a public or private cloud for yourmigration processBoth options have pros, and cons, and the decision ultimately comes down to your company's needs and your risk tolerance. If you move to a public cloud, you gain access to many new features, but also open yourself up to potential security threats if you do not have a strong security framework in place.
ReplyDelete